Brought to you by WorkTime, a monitoring solution designed with privacy, non-invasiveness, and reliability in mind.
October spotlight: cybersecurity awareness month
Every click, email, and login counts when it comes to keeping your company secure. That’s why Cybersecurity Awareness Month, recognized this October across the USA, Canada, Brazil, the UK, South Africa, India, and Australia, is more relevant than ever in 2025. The spotlight is on human behavior, the #1 source of cyber threats. Cybersecurity isn’t just about firewalls anymore. It’s about people, their habits, and everyday workflows. Can you reduce risks without invading privacy? Let’s look at how non-invasive monitoring makes it possible.Employees - the human factor in cybersecurity
Why the focus on employees, not tech issues? Research shows that human errors are responsible for about 95% of cyber incidents. One careless click, reused password, or neglected policy, and even the strongest firewall won’t help. Fatigue, stress, and constant multitasking don’t just hurt productivity. These expose employees to a higher risk of digital threats. A tired employee might click a phishing link, send confidential information to the wrong person, or forget a crucial security step.
- Frequent overtime. When employees work extra hours, mistakes are more likely to happen.
- Phishing risk. Fatigue makes it easier to fall for malicious links.
- Password and data mishandling. Reusing passwords, misplacing files, or accidentally sharing sensitive information can create serious vulnerabilities.
- Overlooked security steps. Skipped updates, unencrypted devices, or ignored company policies leave gaps in protection.
- Remote work blind spots. In hybrid teams, stress or overload can go unnoticed, making errors harder to prevent.
Security challenges for hybrid & remote teams
Remote and hybrid work gave employees freedom, but also a wider attack surface. Once your team leaves the office, your 'secure zone' suddenly includes home Wi-Fi, personal laptops, and cloud tools you can’t always control. Top risks for remote teams include:- Weak networks: Default passwords or unsecured Wi-Fi make it easy for attackers.
- Personal devices: Laptops, tablets, or phones without protection = potential malware entry.
- Workflow gaps: Using unapproved apps, sending sensitive emails to the wrong recipients, or skipping software updates can create serious security gaps.

Why monitoring software matters for cybersecurity
The real threats often start inside your organization with a simple employee error. One reused password, a skipped update, or a lost file can trigger an incident even with top-tier firewalls in place. That’s why monitoring software is so valuable. It helps spot risky patterns early, right in the daily workflow.Balancing monitoring & privacy
Here’s the dilemma: companies need oversight to reduce risks, but excessive monitoring can backfire. Traditional tools often go too far by logging keystrokes, taking screenshots, or recording private messages. Meant to boost control, these practices can create new vulnerabilities. Monitoring logs may store sensitive data, including passwords and personal emails. When compromised, the consequences can exceed the original threat. That’s why privacy-first monitoring is becoming the new standard in cybersecurity.
- No passwords, messages, or personal content are ever collected.
- HIPAA- and GLBA-safe modes support industries handling sensitive information.
- Data minimization ensures only essential performance metrics are stored, nothing more.
Preventing insider threats
Insider threats are tough to catch but costly when they happen. They often come from frustration, fatigue, or overload. Downloading unverified software, sending files to personal devices, or working extra hours may not be malicious, but they can be warning signs. WorkTime helps identify such patterns non-invasively, without turning monitoring into surveillance:- Sudden drops in productivity or focus;
- Long idle periods;
- Use of high-risk or unknown apps.
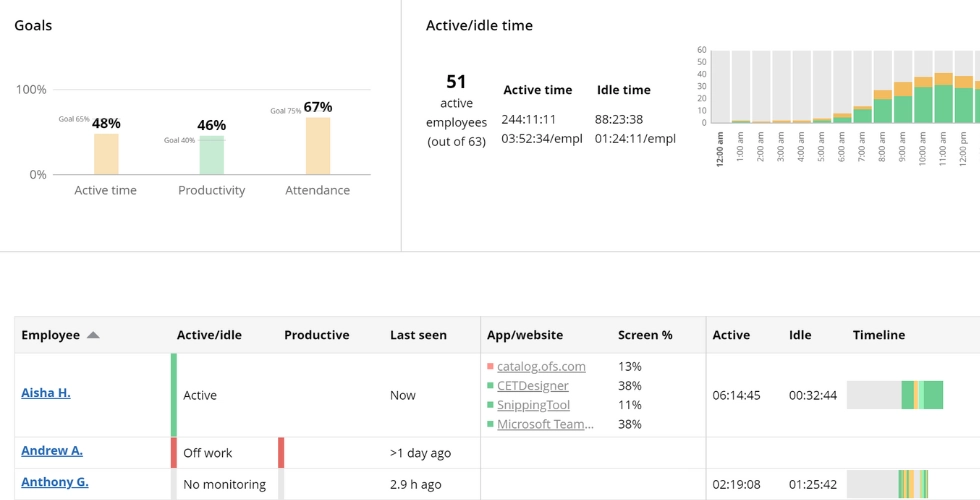

This report provides real-time insights into employee performance. Stay informed while respecting privacy!
Start free trialRegulatory compliance & data protection
Cybersecurity today is also about meeting strict global data protection laws. GDPR, HIPAA, and GLBA require careful monitoring and strong data protection. Imagine a company using invasive monitoring software that records full-screen captures or keystrokes. An employee accidentally types a client’s confidential financial information, which is then stored in the monitoring logs. Exposure of that information may trigger severe financial penalties and long-term brand damage.
How WorkTime reduces risks without invading privacy
So how do you protect data and respect privacy? WorkTime combines security and privacy-first design. This approach helps companies cut down cyber risks without ever compromising personal information. What are the key features that make our monitoring safe and effective?- AES-256 encryption ensures complete security for data.
- Non-invasive monitoring. WorkTime tracks work patterns and productivity without capturing passwords, private messages, or screenshots.
- GDPR-safe mode that is fully aligned with Europe’s strict data protection laws.
- HIPAA-safe mode, designed for organizations handling sensitive health data.
- GLBA-safe mode that is compliant with U.S. financial regulations.
- SOC-2 certification coming soon. We are working toward SOC 2 certification to highlight our dedication to protecting data and following best practices.









