












26
Years of experience
Trusted by 9,500+ global brands and organizations



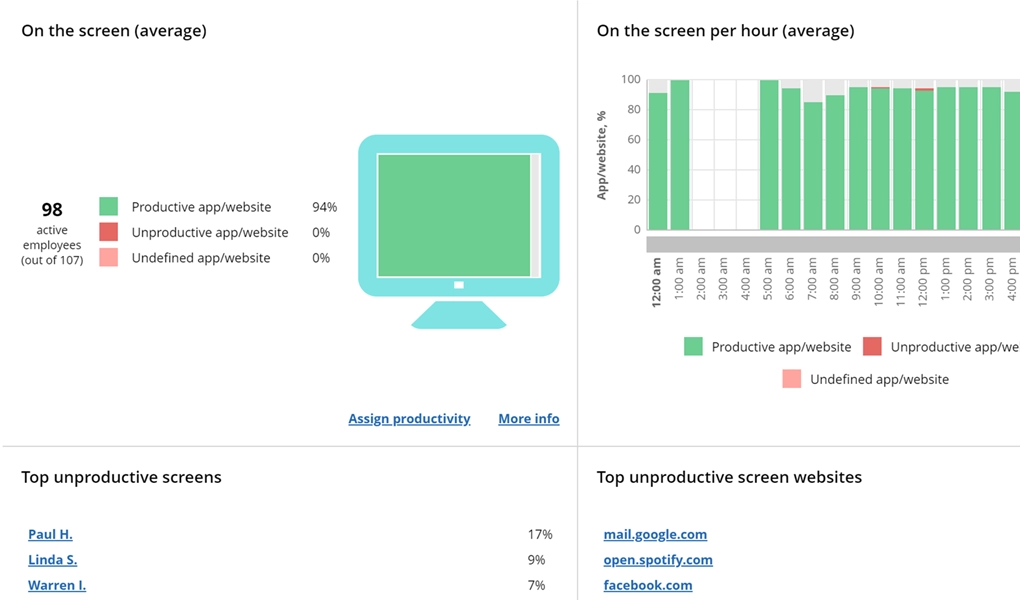
Defense companies choose WorkTime because it does not record any content; it analyzes employee screens numerically. It does not capture any images; it provides numbers. Read what's recorded, what's not.
Read more about non-invasive monitoringDefense companies choose WorkTime because it is stress and failure resistant and has high data safety standards. Additionally, WorkTime offers an on-premise edition, ensuring that the entire WorkTime system and monitoring results stay on the customer's computers.
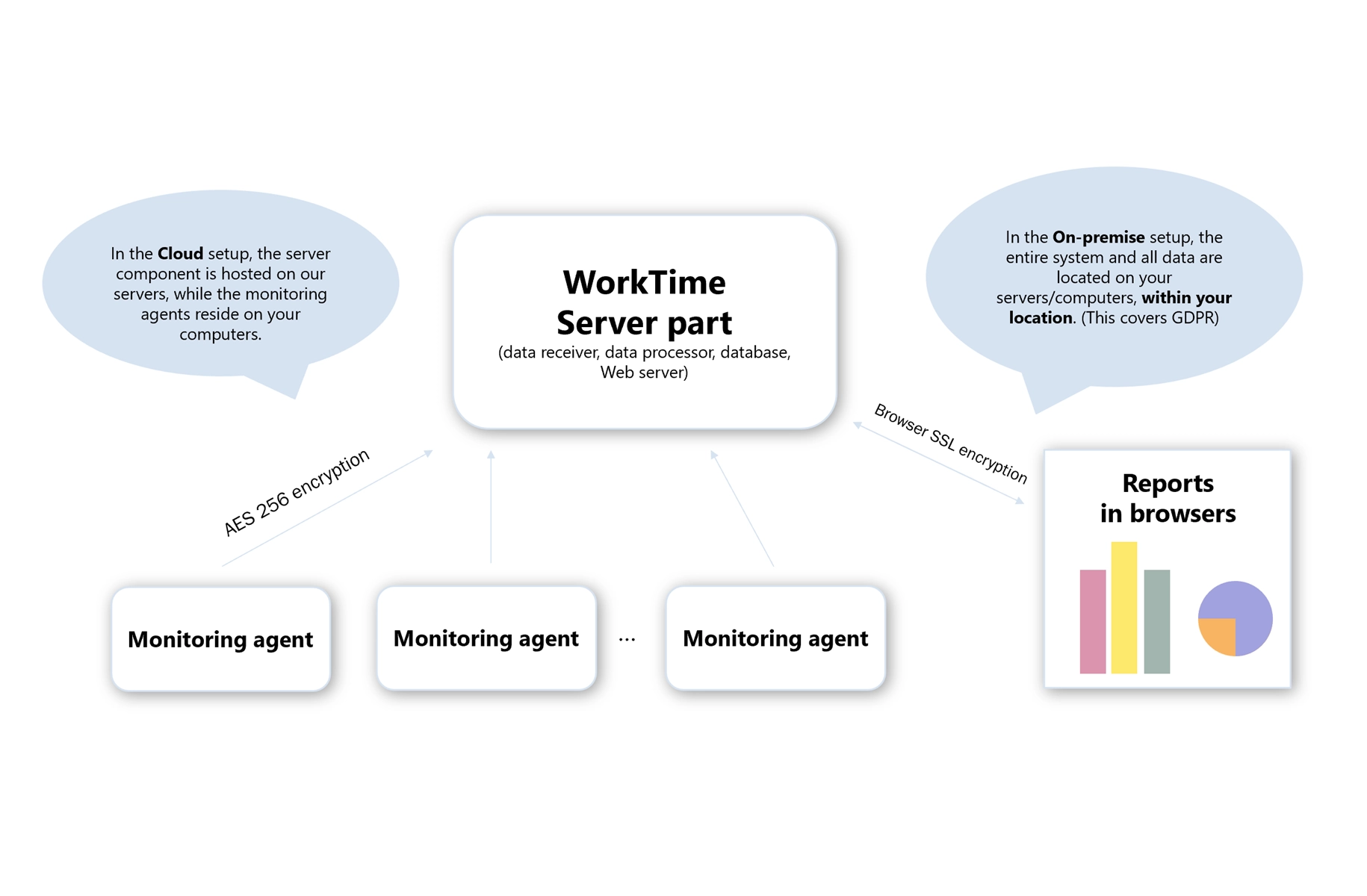
WorkTime trial is all inclusive:
all features, unlimited employees.
No credit card required.
$6.99
/ employee / month billed monthly
$8.99
/ employee / month billed monthly
$10.99
/ employee / month billed monthly
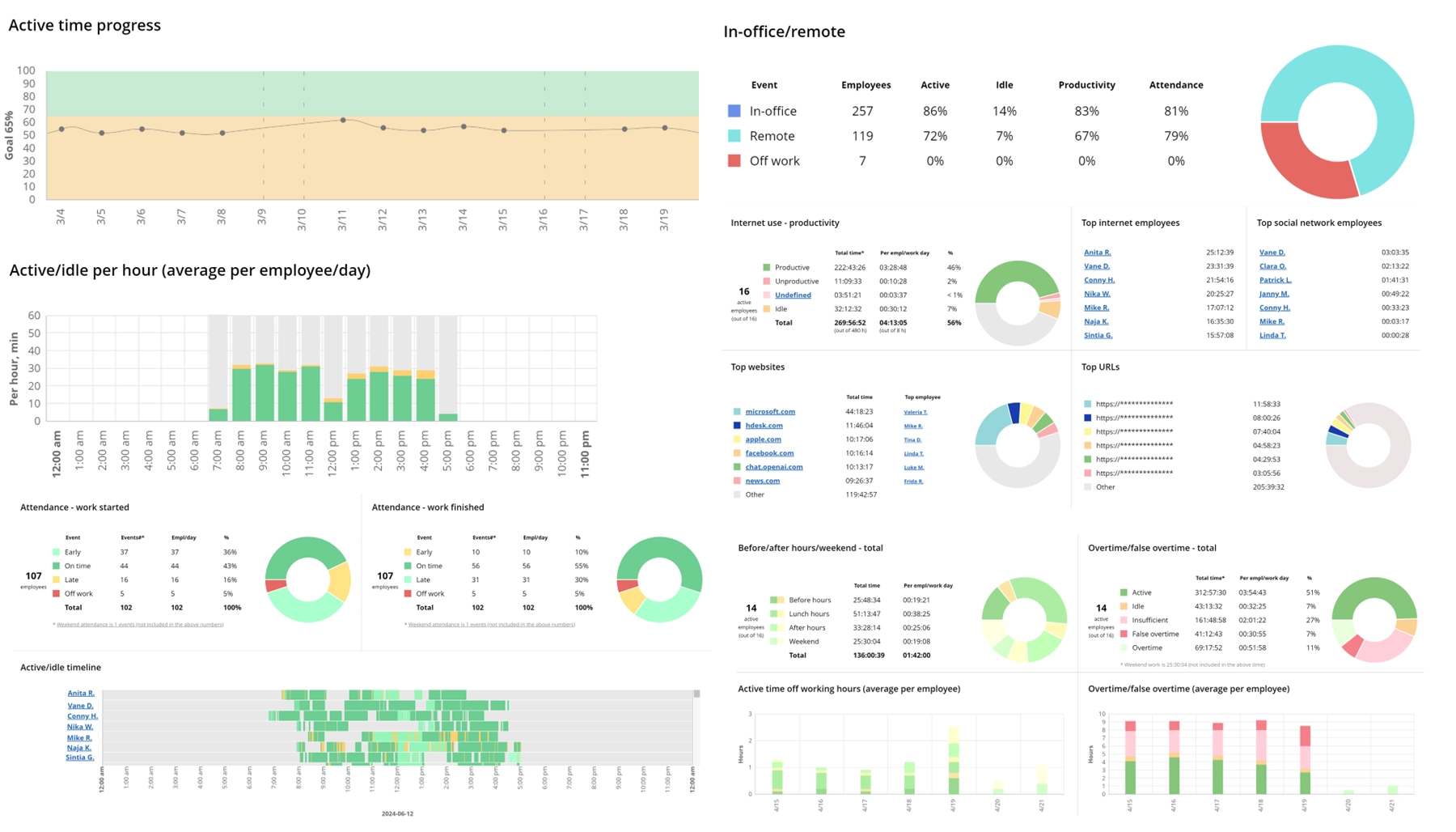
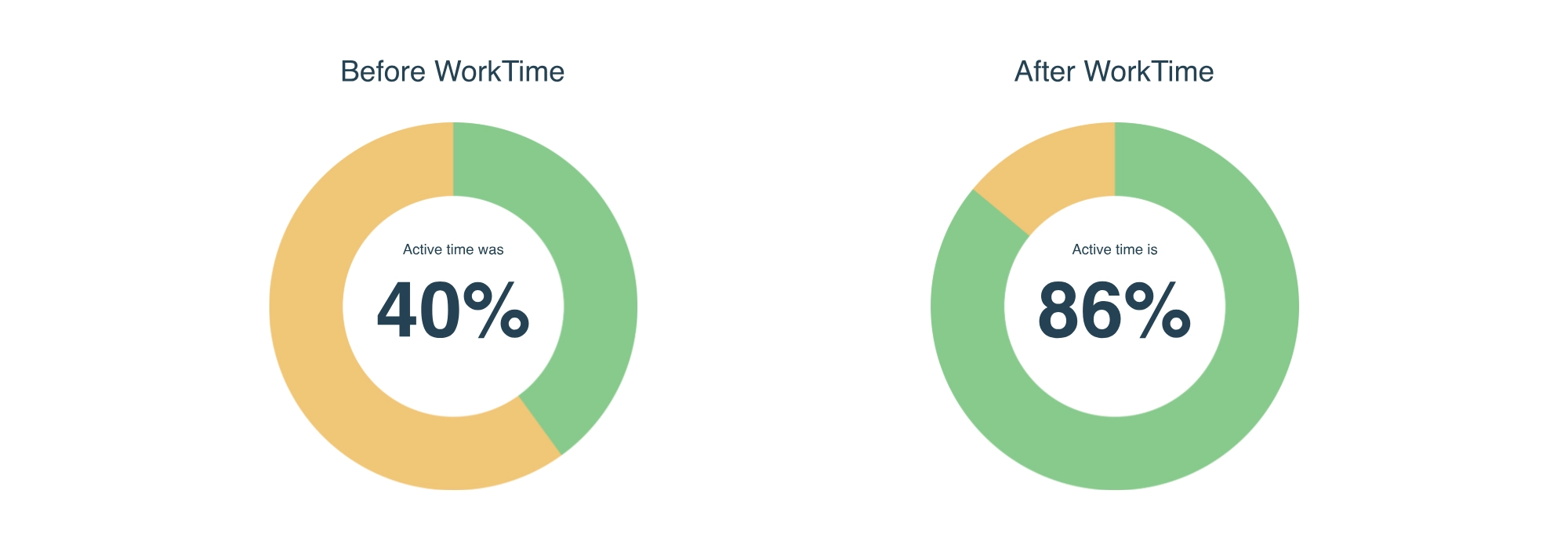
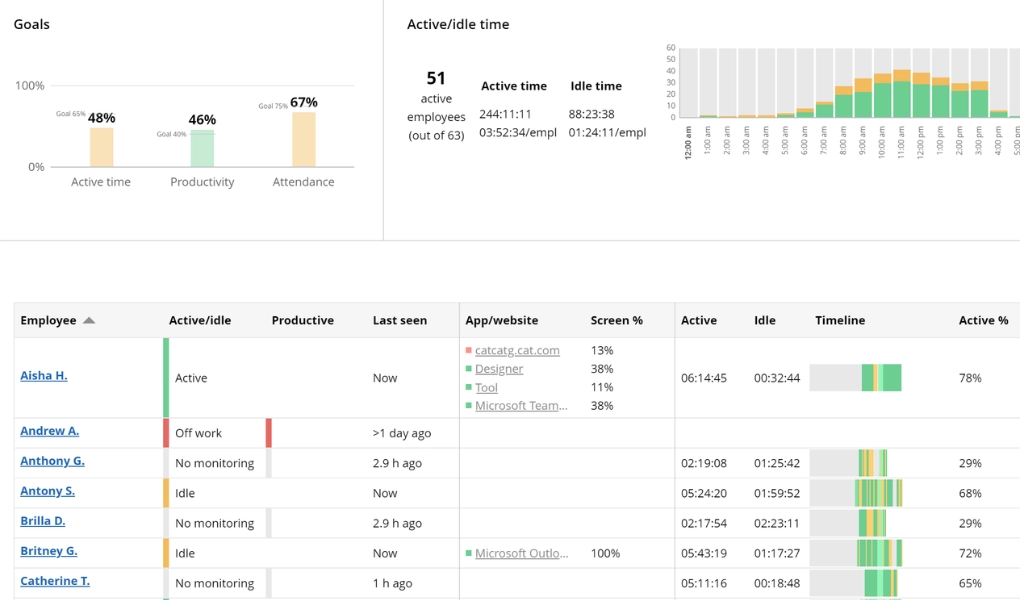
The "What's Now" report from WorkTime shows who is at work, off work, or on vacation; who is active or idle; who is productive or not; and who was late or on time. With WorkTime, you always know what your defense team is doing on the company's computers.