








All employee activity data is securely encrypted both in transit and at rest, safeguarding it against unauthorized access. By applying the same encryption standard trusted by financial institutions and government organizations worldwide, WorkTime guarantees that information remains fully protected while delivering accurate, non-intrusive productivity analytics.
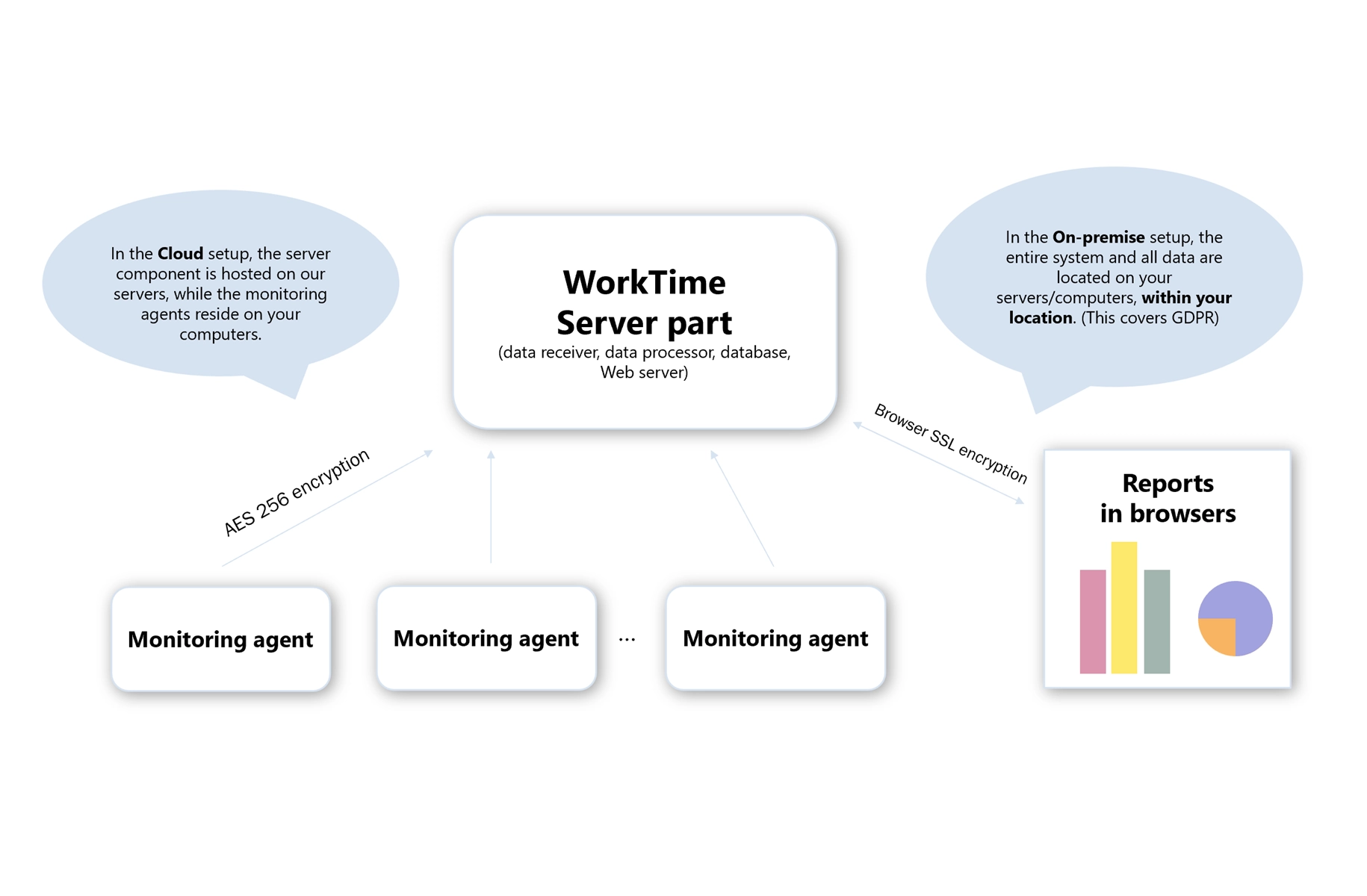
WorkTime applies strong AES-256 encryption to secure all information, whether it is stored on servers or transmitted between systems. This ensures data remains safe from unauthorized access at every stage.
Whether deployed on-premise or in the cloud, all collected data is consistently stored in encrypted form. This guarantees that sensitive business information remains secure regardless of the chosen infrastructure.
WorkTime records only essential metadata needed for productivity analysis. It never captures passwords, message texts, or the content of communications, ensuring full respect for employee privacy.
Organizations retain complete authority to configure and manage all security settings within WorkTime, aligning data protection practices with their internal policies and compliance requirements.
This design guarantees that monitoring data is never lost and the monitoring process remains stable, even under heavy workloads. Proven in real-world deployments, WorkTime has been successfully implemented in organizations ranging from small teams to enterprises with 15,000+ employees and environments with over 300 Citrix servers.
WorkTime trial is all inclusive:
all features, unlimited employees.
No credit card required.
$6.99
/ employee / month billed monthly
$8.99
/ employee / month billed monthly
$10.99
/ employee / month billed monthly
WorkTime follows SOC 2 principles to ensure data security, availability, and confidentiality. By adhering to industry-recognized auditing standards, WorkTime demonstrates reliable safeguards for handling sensitive business information. This gives organizations confidence that their monitoring data is managed with strict controls and operational integrity.
Learn moreWorkTime is designed with healthcare organizations in mind, offering a HIPAA-safe mode that ensures protected health information (PHI) is never collected or exposed. The system monitors productivity through metadata only, without accessing electronic health records, patient data, or private content. This makes WorkTime a secure solution for healthcare providers that must comply with HIPAA requirements.
Learn moreWorkTime fully supports GDPR requirements by applying privacy-first monitoring practices. The software collects only the data necessary for productivity reporting, encrypts all information, and gives customers complete control over their data. Employees’ personal content, messages, and credentials remain private, ensuring transparency and trust in compliance with GDPR standards.
Learn moreWorkTime is built on a non-invasive approach to employee monitoring. It never records passwords, message texts, screen content, or private files. Instead, it focuses exclusively on activity metadata, which is sufficient to generate 70+ productivity and workforce analytics reports. This privacy-first design ensures that organizations receive the insights they need without intruding on employee confidentiality.
Learn moreWorkTime is green employee monitoring software — designed to boost productivity while respecting privacy.
Safe screen analyzer, safe keystroke counter, productivity monitoring


