Here are a few costly mistakes that could have been easily avoided with WorkTime:
1. Using screenshots as an office leaderboard cost one employer $100K Use WorkTime leaderboards - safe and effective 2. A former administrator hack caused $1.1 million in damage Don't capture unnecessary data - use WorkTime to measure employee productivity 3. One businessman’s $90,000 stolen with malicious software Use WorkTime monitoring - it offers a safe alternative to screenshot monitoring 4. A law firm underwent a turnover crisis due to intrusive screenshot monitoring Use transparent monitoring & retain valuable employees 3 reasons why screen capture employee monitoring harms your business Productivity breakthrough is real without screenshots and keystrokesThis article has been prepared by WorkTime, experts in employee monitoring with over 20 years of experience. WorkTime offers safe, legal, and ethical monitoring software that protects your business while ensuring an instant productivity boost.
Why do employers monitor employees?
Employers monitor employees to ensure productivity, task completion, and timely execution. Employee productivity tends to decline over time in the office, and even more so for remote employees, where direct supervision by a manager is absent. Based on our over 20 years of experience in employee monitoring software development, we have received extensive feedback from our customers. The reality is that before implementing WorkTime, employee computer active time averages around 36-40% (which is less than 4 hours in an 8-hour workday). However, after WorkTime is applied, active time quickly increases to 75-90% within just a few days. Is it worth monitoring employees? The answer is a clear "yes."Why do employers monitor employees? Because monitoring boosts employee computer active time from 36-40% to 75-90% within just days!
Why is screenshot monitoring not only bad but also ineffective?
Why is screenshot monitoring bad? Because it can harm your business in many ways. Below are a few examples outlined in this article: 1. Privacy disclosure cost employer $100K 2. Web banking data leakage: former employee sued Canadian IT enterprise 3. Fired manager sabotages employer, causing $1 million damage What's the first thing that comes to mind when you read such headlines? Probably, it looks like attention grabbers. Unfortunately, these are real-life cases everyone could face when implementing keystroke and screenshot monitoring.Real-life cases provide strong evidence against screenshot monitoring.You need to understand this: when employees use company computers, especially laptops, they often access a lot of private information, such as banking, insurance, and health details. They also discuss personal matters involving family, friends, and more. All of this information will be captured by screenshot and keystroke monitoring functions and stored in your database. Even if you don’t plan to display it on office screens, can you guarantee that it won’t leak from the database?
When employees use company computers, especially laptops, they often access a lot of private information.Why is screenshot monitoring ineffective? Because it doesn’t contribute to monitoring or improving employee productivity. There are far more safe and effective ways to enhance productivity KPIs through monitoring. Employee monitoring can be a powerful tool—when you use the right approach.
There are far more safe and effective ways to enhance productivity KPIs through monitoring.
Does safe and effective employee monitoring exist?
Yes, it does. Safe and effective employee monitoring measures key performance indicators (KPIs) such as active time, attendance, productivity, time spent in online meetings, focus level, burnout score, and more. None of these KPIs require monitoring screen content, such as screenshots or keystrokes. This is the approach we’ve followed at WorkTime for years. WorkTime is a safe and effective employee monitoring software.None of the employee performance KPIs require monitoring screen content, such as screenshots or keystrokes. WorkTime is an example of a safe and effective employee monitoring software.
Here are a few costly mistakes that could have been easily avoided with WorkTime:
1. Using screenshots as an office leaderboard cost one employer $100K
One Reddit user shared his experience in a company with over-excessive workplace surveillance. His boss believed negative reinforcement was the most powerful tool to increase productivity. That’s why he applied screen capture employee monitoring and decided to display screenshots as a slideshow on a 50’’ TV. It’s important to mention that the employer’s computer was also a part of this so-called “experience”. No one could predict what would happen next. Instead of a productivity boost, the boss received a series of lawsuits. What was the reason? So many things went wrong when they started to record employee computer screens. Together with work-related screens, a lot of sensitive information was displayed on the company’s wall. Employees revealed who was raised (including the sum), read emails related to their colleague's divorce, and even spotted someone’s drug test results.Screenshots displayed on the company's wall revealed a lot of sensitive information.The most shocking detail is that employees could snap a picture of whatever was on the screen. Once, the social insurance details randomly appeared on the slide after the screenshot of an email notification that a project manager would be fired right after completing his tasks. It is not a surprise that the company’s CEO received multiple lawsuits from his fired employees that cost him approximately $100K.
Use WorkTime leaderboards - safe and effective
You can try noninvasive monitoring software to boost motivation in a more safe and employee-friendly manner. For instance, we offer WorkTime leaderboards. This report can be used as an element of workplace gamification to foster team motivation. Moreover, it focuses solely on valuable metrics related to employee performance, without including any recorded content.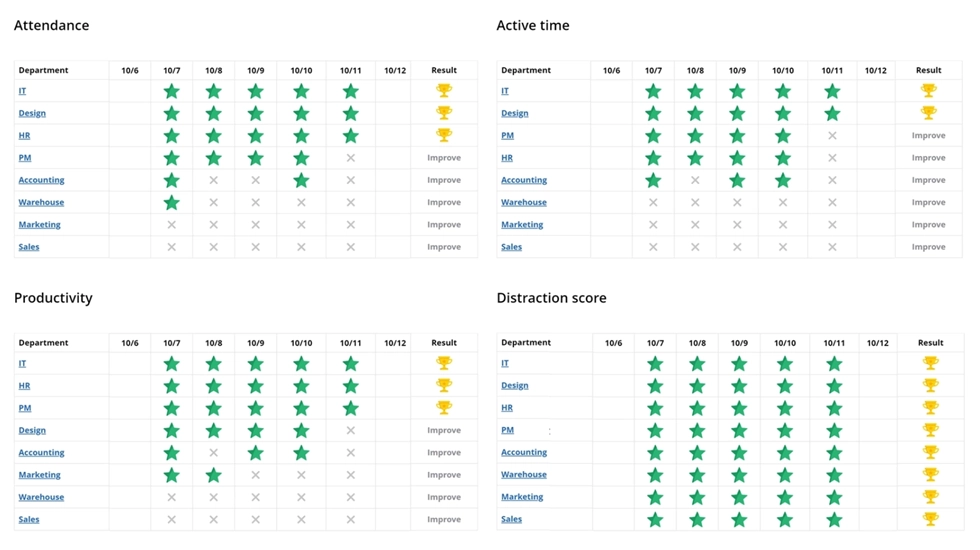

Motivate your team with WorkTime leaderboards! This report displays the company's achievements, highlighting each department’s KPIs. You can add leaderboards to the newsletter or keep this report on the wall to inform employees about goals, achievements, and areas for improvement.
Start free trial2. A former administrator hack caused $1.1 million in damage
This case took place in an American factory. A fired system administrator accessed the company’s servers and altered the control systems, causing a series of delays. A two-week-long attack cost the paper factory owner about $1.1 million in damage. A former employee used login credentials that were still valid after he was dismissed. What if your employee, who has access to screenshots and keystrokes monitoring reports, decides to sabotage your company? Such sensitive information as employees' passwords, private pictures, web-banking details, health-related information, or personal chat content can be captured with a keystroke and screenshot monitoring software. In most cases, you are at risk of receiving numerous lawsuits.Don't capture unnecessary data - use WorkTime to measure employee productivity
WorkTime non-invasive monitoring software guarantees 100% data security. We do not record any content. Instead of capturing screenshots and recording keystrokes, our software evaluates employee productivity in numbers. For example, our Internet use monitoring reports categorize websites as productive or unproductive, providing valuable insights based on statistics.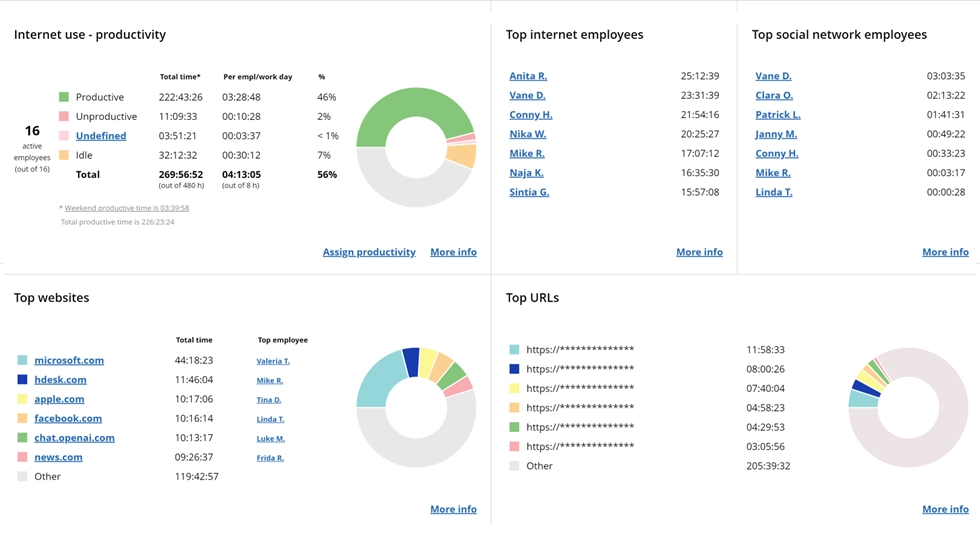
Here you can see the productivity of the department during a certain period. WorkTime categorizes all websites and apps as either productive or unproductive. With this report, you can effortlessly detect areas for improvement and increase team productivity level.
Book demo3. One businessman’s $90,000 stolen with malicious software
Imagine you open your bank account and all your money is gone. This shocking situation came into reality for a Florida businessman who lost $90,000 in one moment. In the course of the legal process, it was found that his computer had been infected with malicious software that captures screenshots, records keystrokes, and sends this information to unknown hackers. The matter is that monitoring software with a keystroke counter feature works similarly to malware, being a potential threat to private information security. The only difference is in the field and purpose of use. Thus, implementing keylogging monitoring software may cause employees' private information leakage.Use WorkTime - it offers a safe alternative to screenshot monitoring
WorkTime is a risk-free and efficient alternative to keystroke monitoring software. We do not offer logging keystrokes or screenshot monitoring features. In WorkTime, traditional invasive screenshots have been replaced with a non-invasive "Screen productivity" report: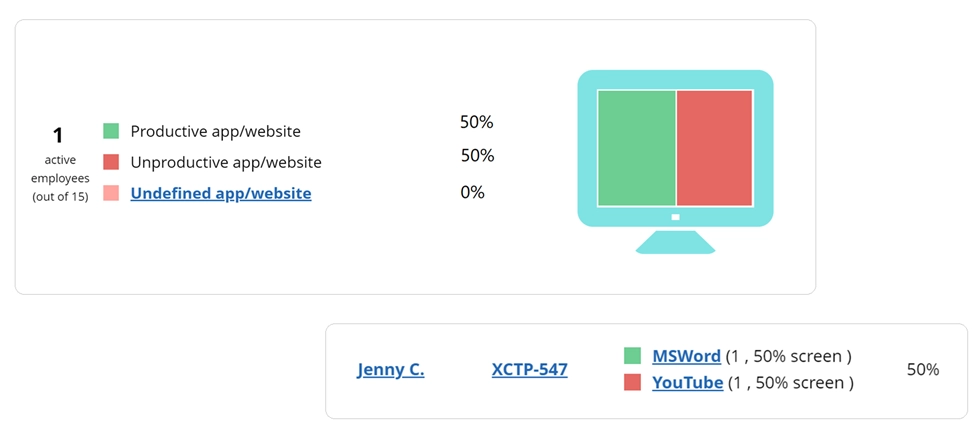

The "Screen Productivity" report analyzes employee screen usage in numbers, without capturing any content. It displays the percentage of the screen occupied by productive and unproductive apps and websites. Additionally, it provides a history of all screen apps and websites, marking them as productive or unproductive, along with the percentage of the screen each occupies.
Start free trial4. A law firm underwent a turnover crisis due to intrusive screenshot monitoring
One of our clients shared this story. The attorney agency underwent a turnover crisis during the pandemic times. Employees quit one by one without stating the reasons. The situation was getting worse, as a personnel shortage resulted in a revenue decline. The law firm lost thousands of dollars and potential clients. Moreover, hiring expenses increased significantly. Managers took the situation seriously after the lawyer responsible for consulting VIP clients decided to quit. Fortunately, this employee agreed to provide detailed feedback, explaining that implementing an excessive surveillance system with continuous real time screen monitoring was the core reason to break the contract. The process was so stressful and counterproductive that the lawyer had no motivation to continue working in such an environment. This is what he mentioned in his feedback: “Honestly speaking, I felt that I was mistrusted and unvalued. I did not expect that after 5 years I worked here, a manager would evaluate my effectiveness by taking these annoying screenshots every 10 minutes instead of considering the number of satisfied clients and the profit I brought to the agency.”Invasive monitoring makes employees feel mistrusted and unvalued.Indeed, the surveys confirm that tracking software is among the top reasons for leaving the company.
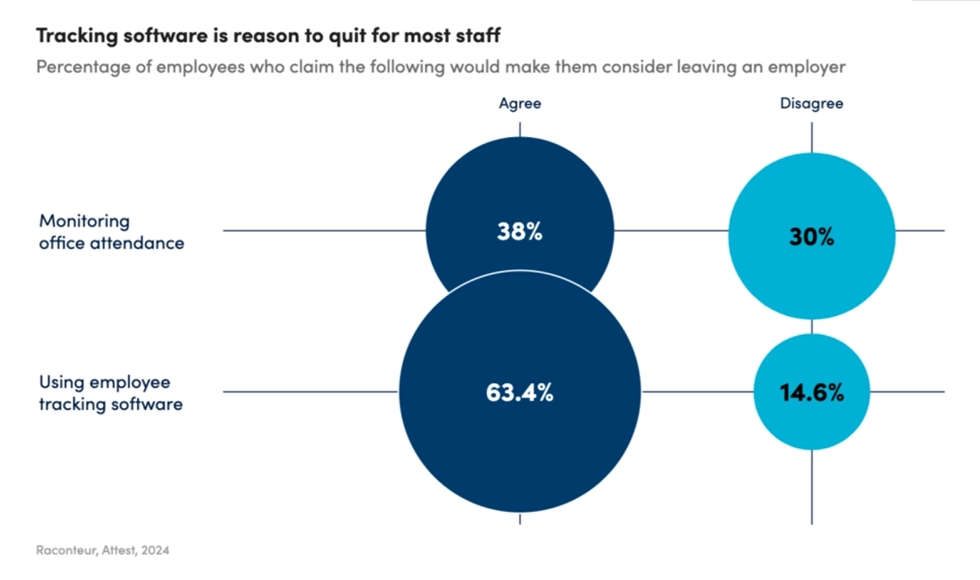
Source: Raconteur
63% of employees are likely to quit a company that applies employee tracking software. Just imagine how significantly this percentage will increase if to clarify that the employer uses screenshots and keylogging monitoring software.








