#1 Non-invasive monitoring
For Windows, macOS
Terminal/Citrix
Cloud, on-premise
1 to 15,000+ computers
In-office, hybrid, remote





26
Years of experience
Trusted by 9,500+ global brands and organizations


WorkTime is Green UAM software is the only non-invasive monitoring on the market. All invasive functions are replaced by safe, non-invasive alternatives.
Safe for any country & industry
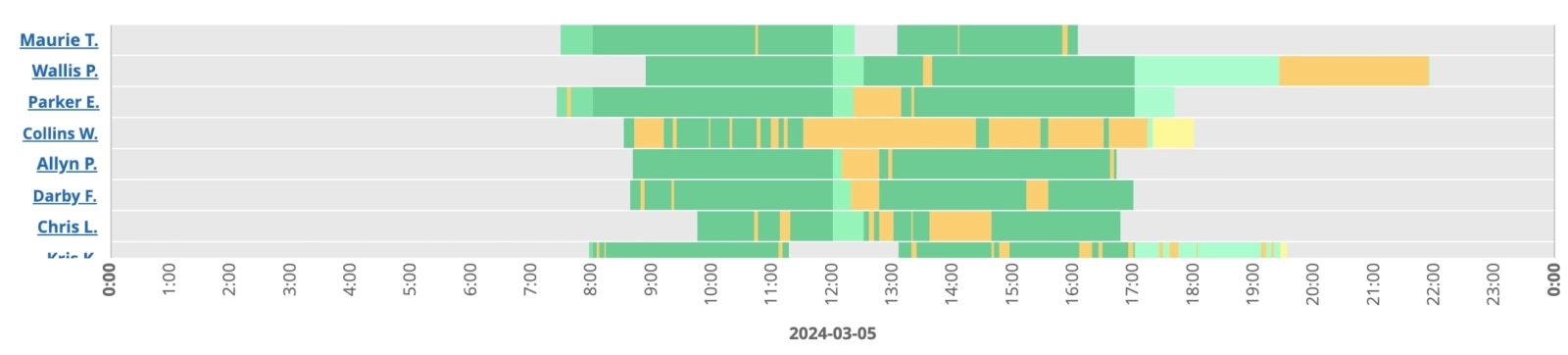
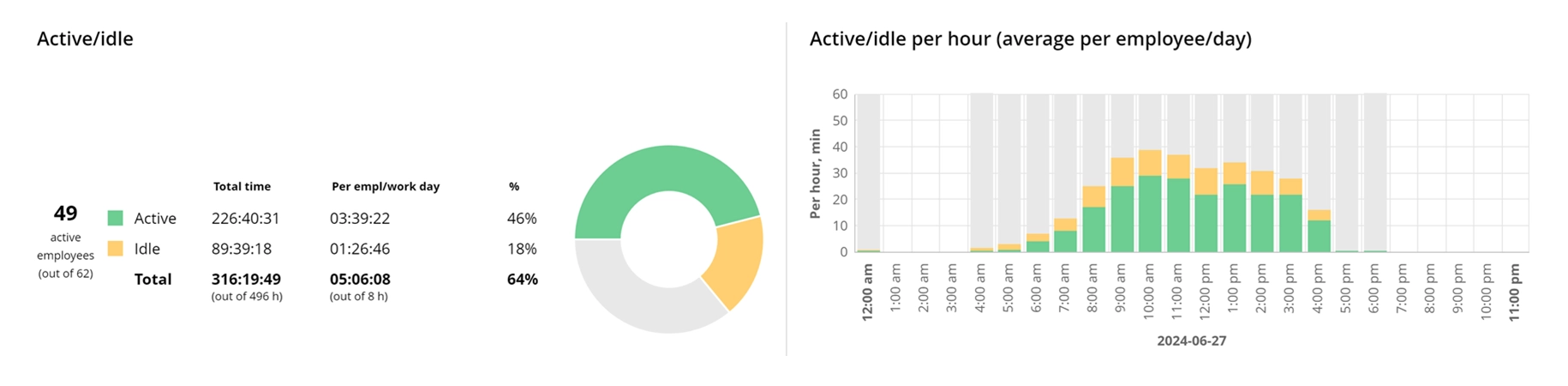
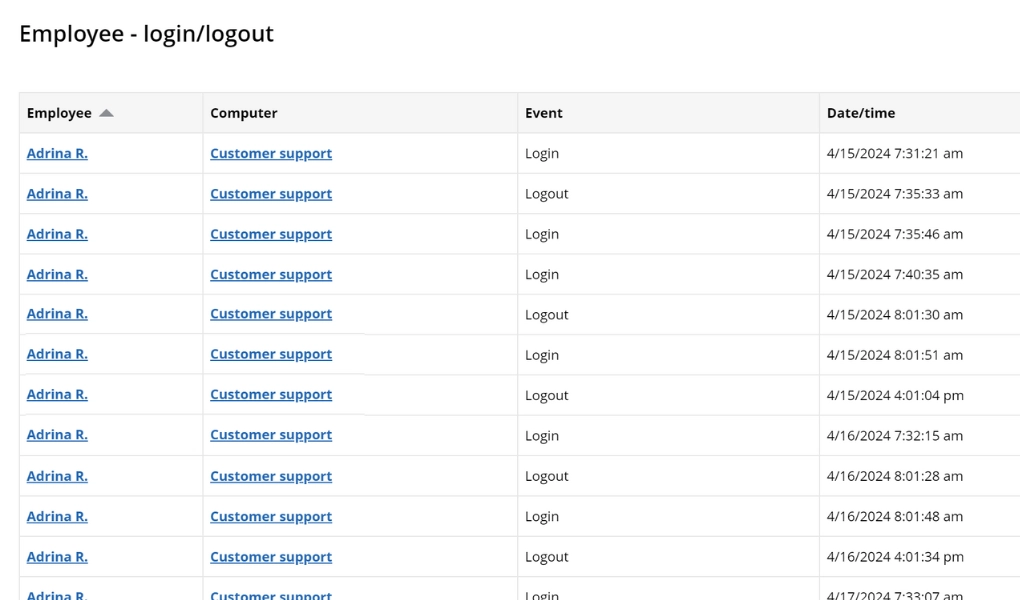
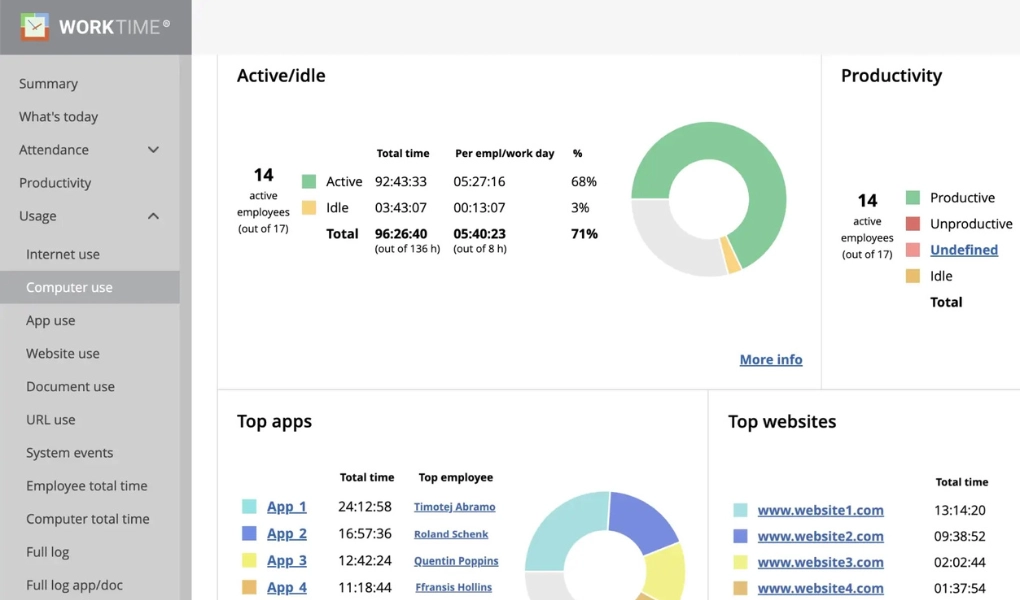
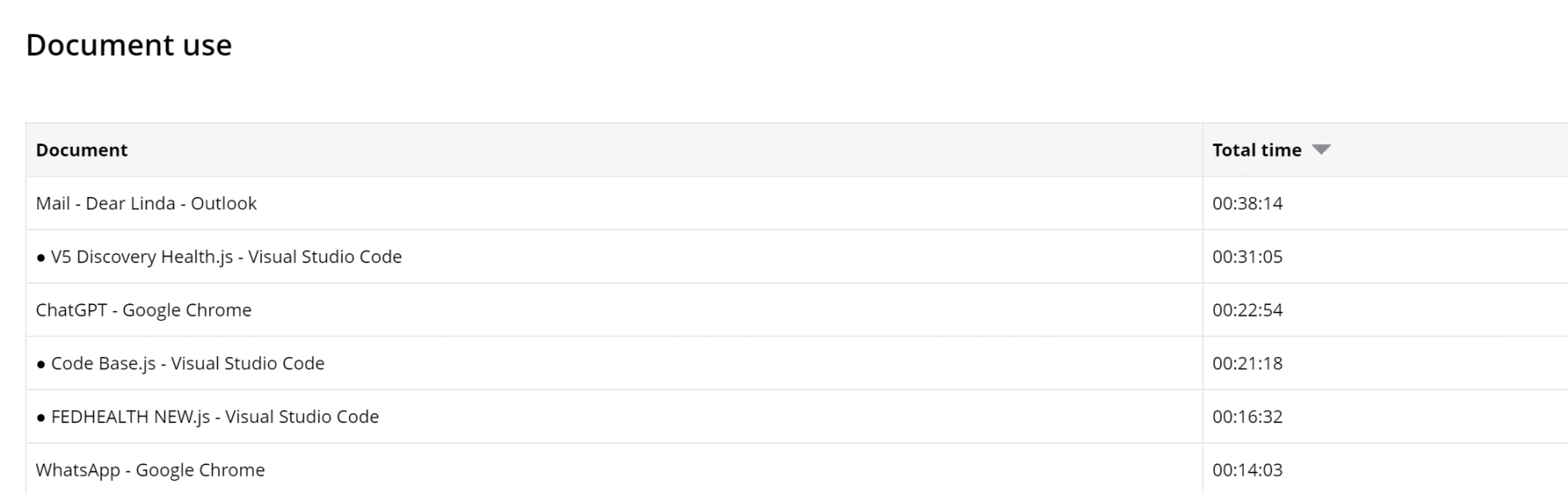
WorkTime monitors user activities such as application and document usage.

Banking
170
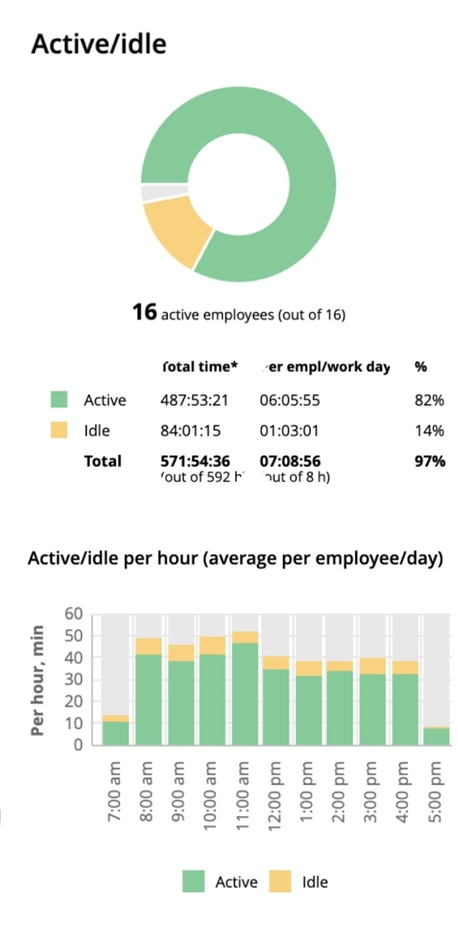
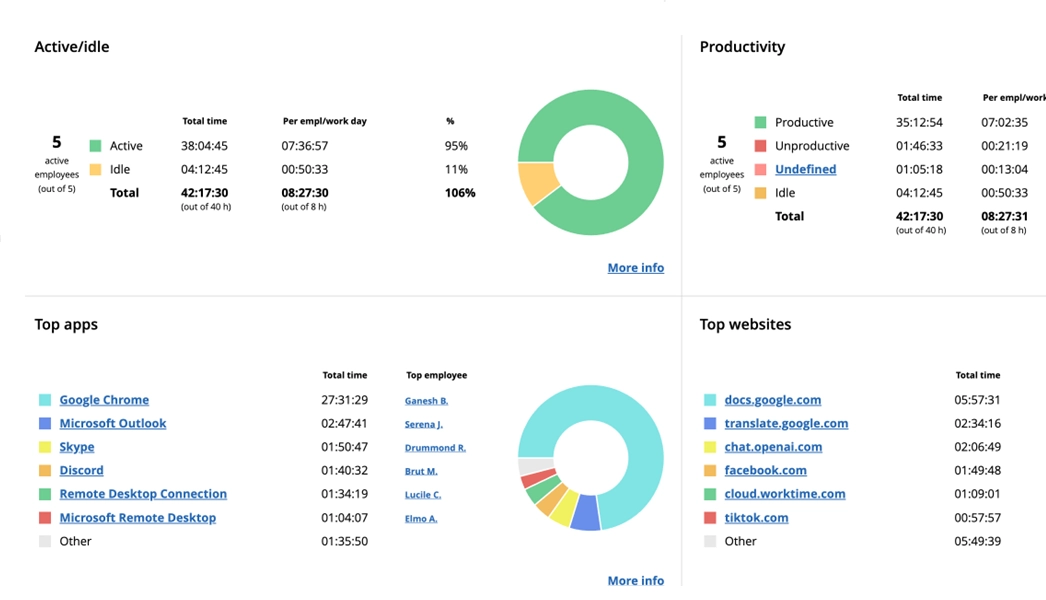
This UK bank managed to increase their remote employees' active time by 46% in just 3 days! WorkTime functions and it's transparent approach made it smooth and effective.
Read moreExcellent boost!