For Windows, macOS
Terminal/Citrix
Cloud, on-premise
1 to 15,000+ computers
In-office, hybrid, remote





26
Years of experience
Trusted by 9,500+ global brands and organizations

Banking
500
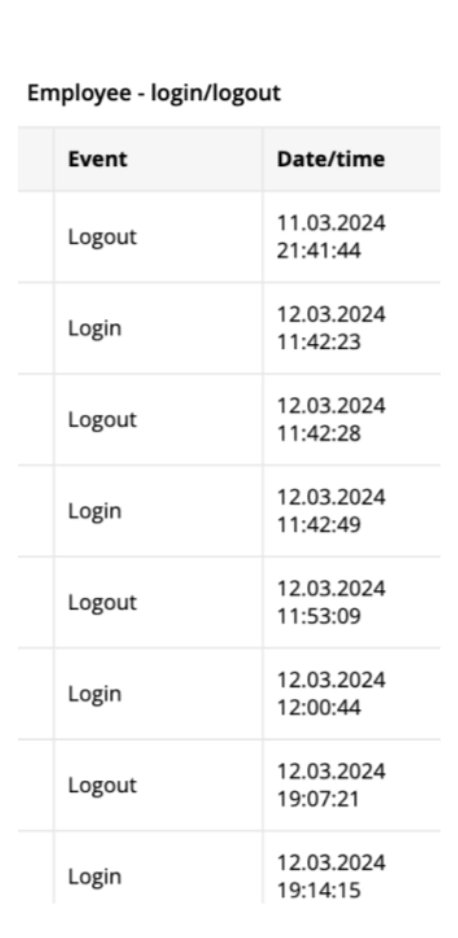
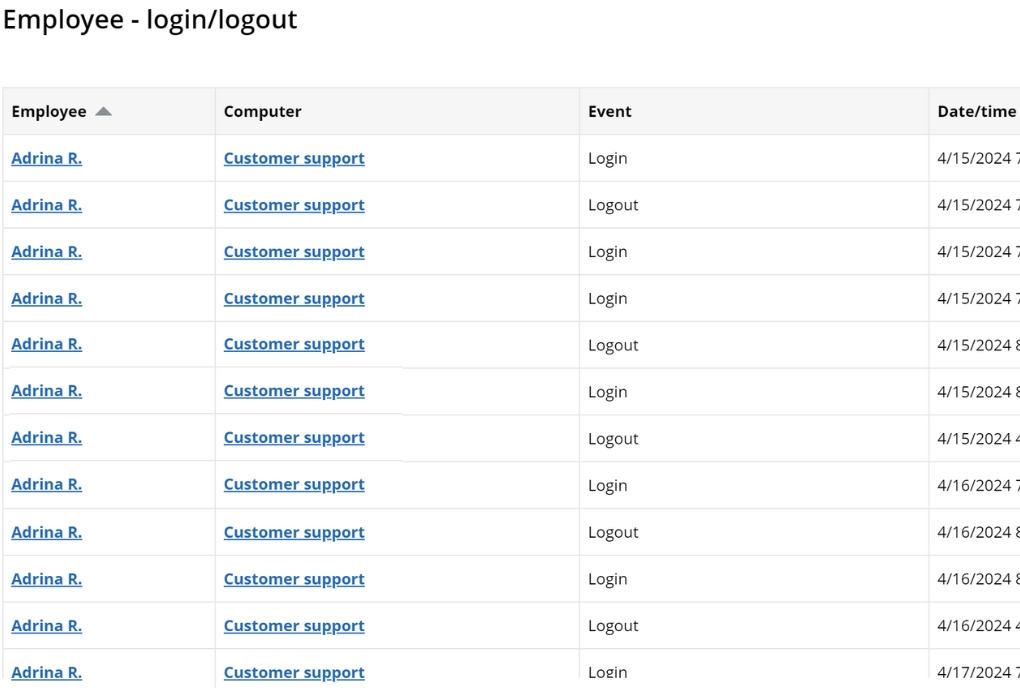
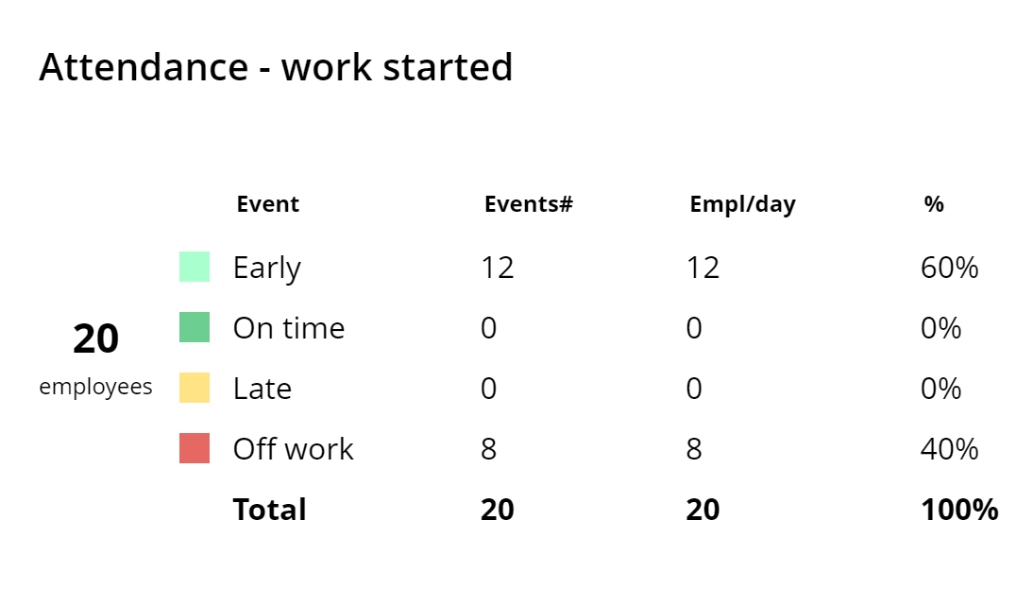
Checking in does not imply attendance. Employees at this Spanish bank manipulated the check-in card system. Instead of physically coming to work, they would pass their cards to coworkers to swipe for them. The bank used WorkTime login-logout reports to verify employee check-ins.
Read more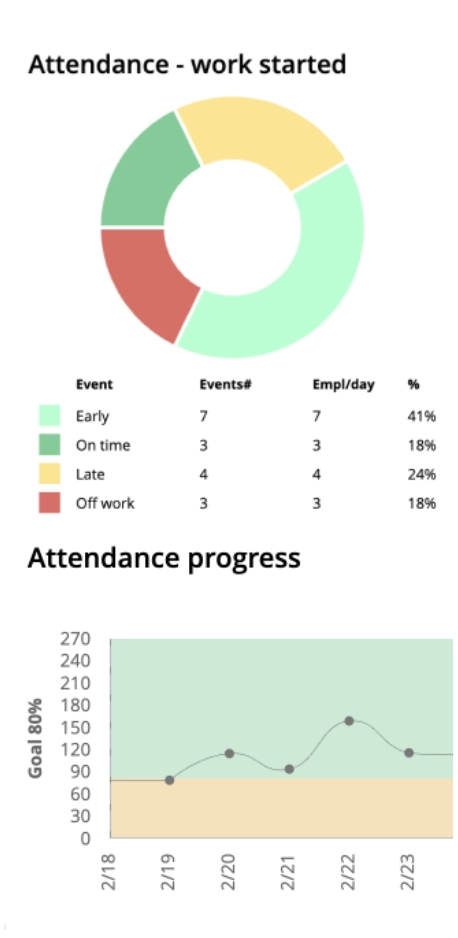
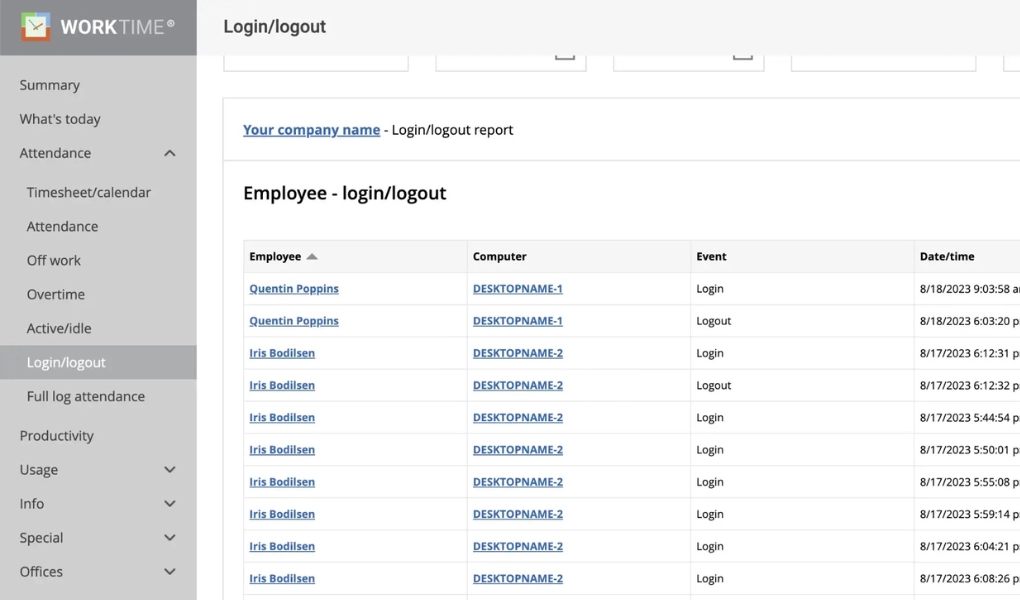
WorkTime is Green login/logout monitoring software, the only non-invasive monitoring on the market.
GDPR compatible
On the company's computers, monitor employee logins and logouts as well as active time during lunch time, before and after hours, and on weekends.

Telecom
20+
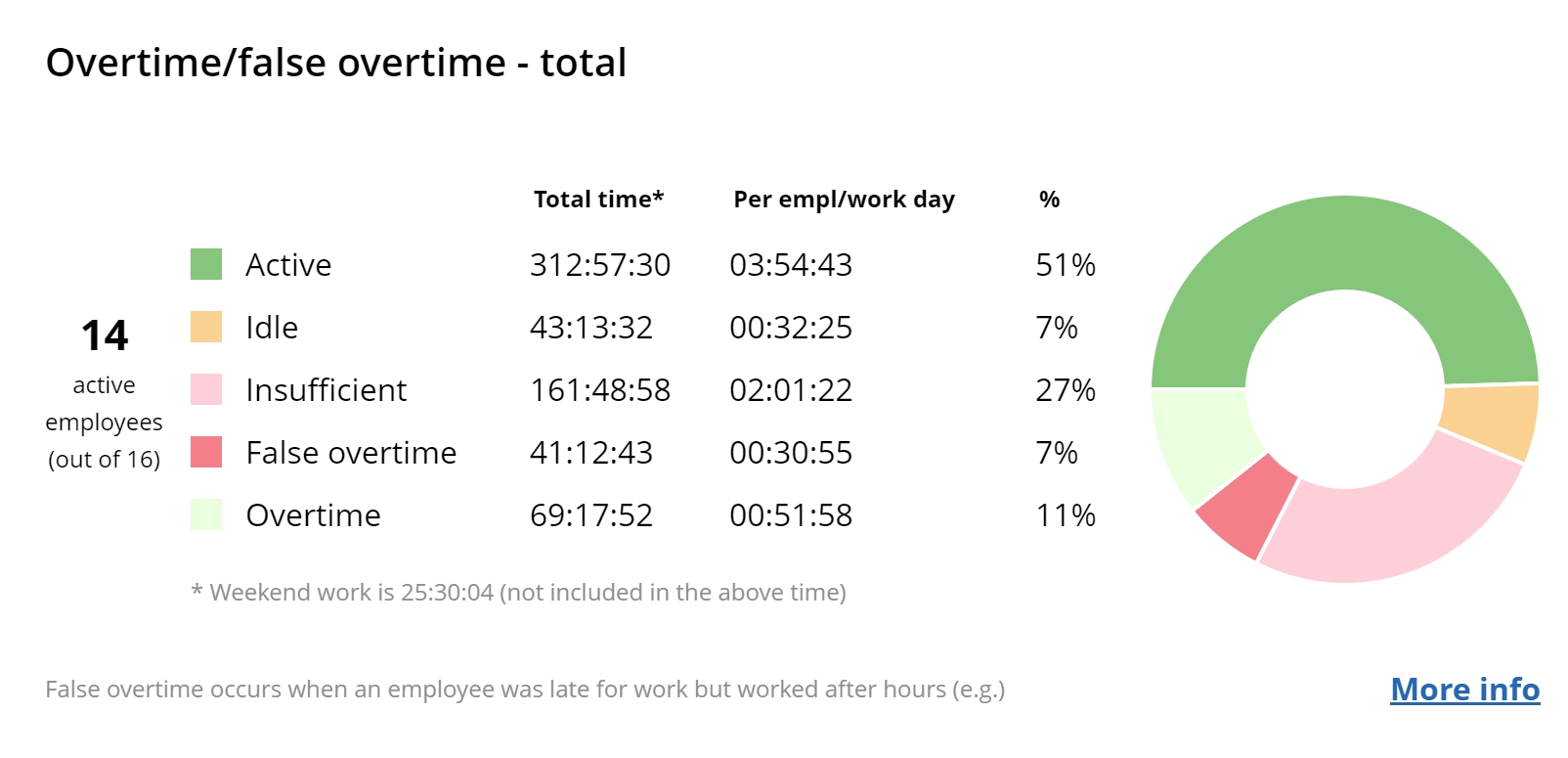
This South African telecommunication company successfully utilized WorkTime to more than double its team performance. They significantly enhanced attendance from 36% to over 105%, active time from 39% to more than 97%, and productivity from 40% to over 95%.
Read moreProductivity from 40% to 95%!